This is post #25 of our Build Flows Faster series, covering our new utility actions for Power Automate. Today’s lesson covers how to encrypt an decrypt data in Power Automate with the ‘Utility – AES Encryption‘ and ‘Utility – AES Decryption‘ Encodian utility actions.
Our utility actions are targeted at helping you build flows more quickly with less complexity. They brilliantly only use 0.05 actions from your Encodian Flowr subscription allowance. For example, under a standard plan that permits 500 actions per month (uses), you could use the utility actions 10,000 times!
As the action names imply, the ‘Utility – AES Encryption‘ and ‘Utility – AES Decryption‘ utility actions are used to encrypt (secure) and decrypt data. Now, you may pick-up that we offer two types of encryption within Encodian utility actions:
There are lots of explanations available in the usual locations, however to summarise; AES is a symmetric algorithm using a single key for both encryption and decryption, making it fast for bulk data encryption, while RSA is an asymmetric algorithm using a pair of keys (public and private) primarily for secure key exchange.
Considering the above we’re focussing today on how we can encrypt / decrypt data using Power Automate, and we’ll use AES encryption for this purpose.
As with many of our utility actions, there are many scenarios where you may need to encrypt / decrypt data. Therefore, we’ll focus on how the ‘Utility – AES Encryption‘ and ‘Utility – AES Decryption‘ Encodian utility actions work instead of focusing on a specific use-case.
We’re going to create an encryption flow and a decryption flow! Which should provide a good working examples which can be integrated into your own Power Platform Solutions.
Consider the following basic and manually triggered flow:
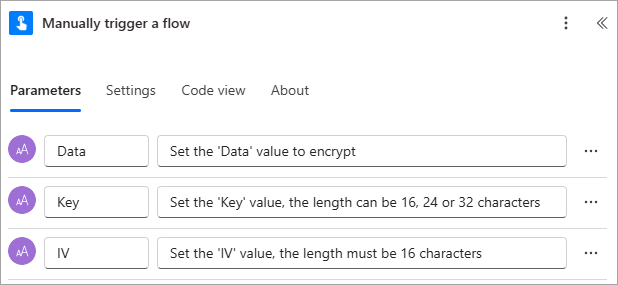
Upon triggering the flow, the user will be prompted for the following values:
1. Add the ‘Utility – AES Encryption‘ utility action
1.a Data: Select the ‘Data’ property provided by the trigger action
1.b. Output Type: Select ‘BASE64’
1.c. Key: Select the ‘Key’ property provided by the trigger action
1.d. Mode: Select ‘CBC’
1.e. Initialization Vector: Select the ‘IV’ property provided by the trigger action.
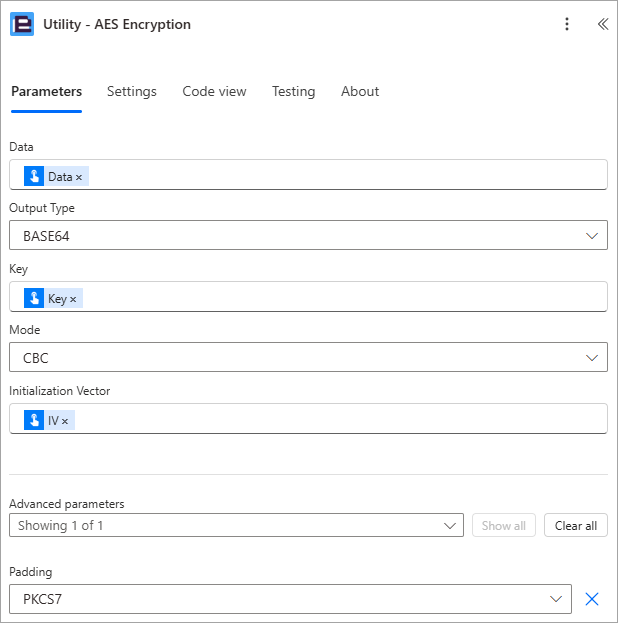
The ‘Utility – AES Encryption‘ utility action will return the data value encrypted and contained within the ‘Result’ property. For demonstration purposes I will send the ‘Result’ property in an email to the user who triggered the flow.
Add and configure the ‘Send and email notification (V3)’ action as required, noting that when using the new Power Automate user interface the ‘User email’ property provided by the ‘Manually trigger a flow’ action is encoded as a base64 value which must be converted to a string using the ‘base64ToString’ expression as detailed below:
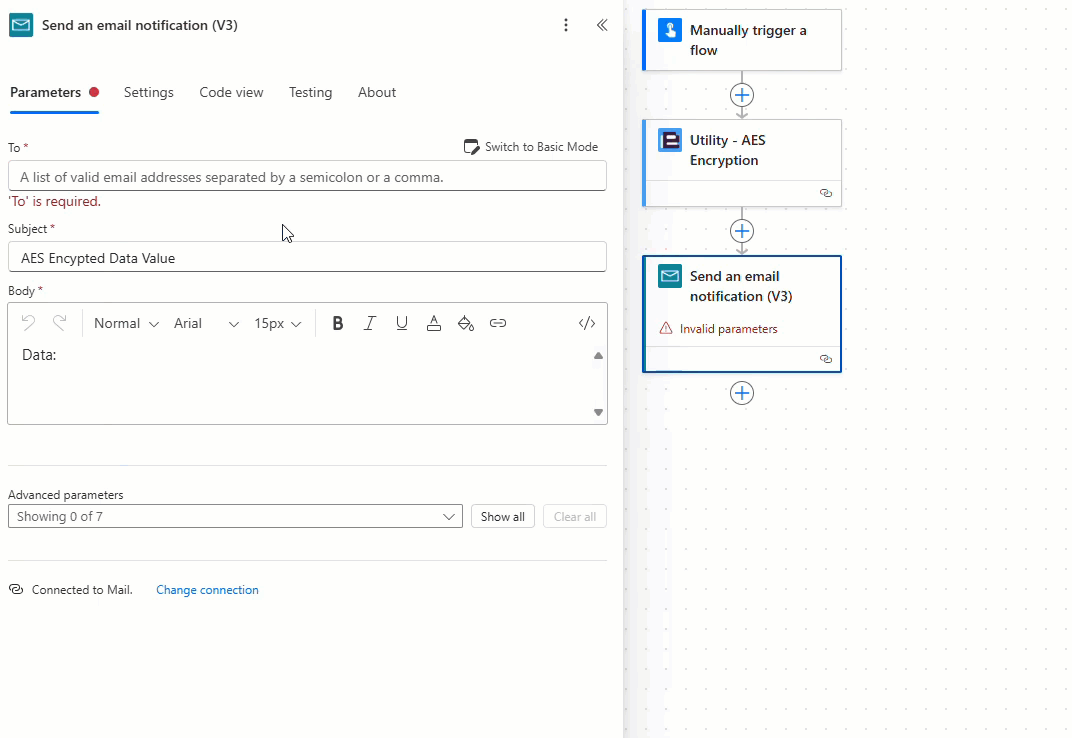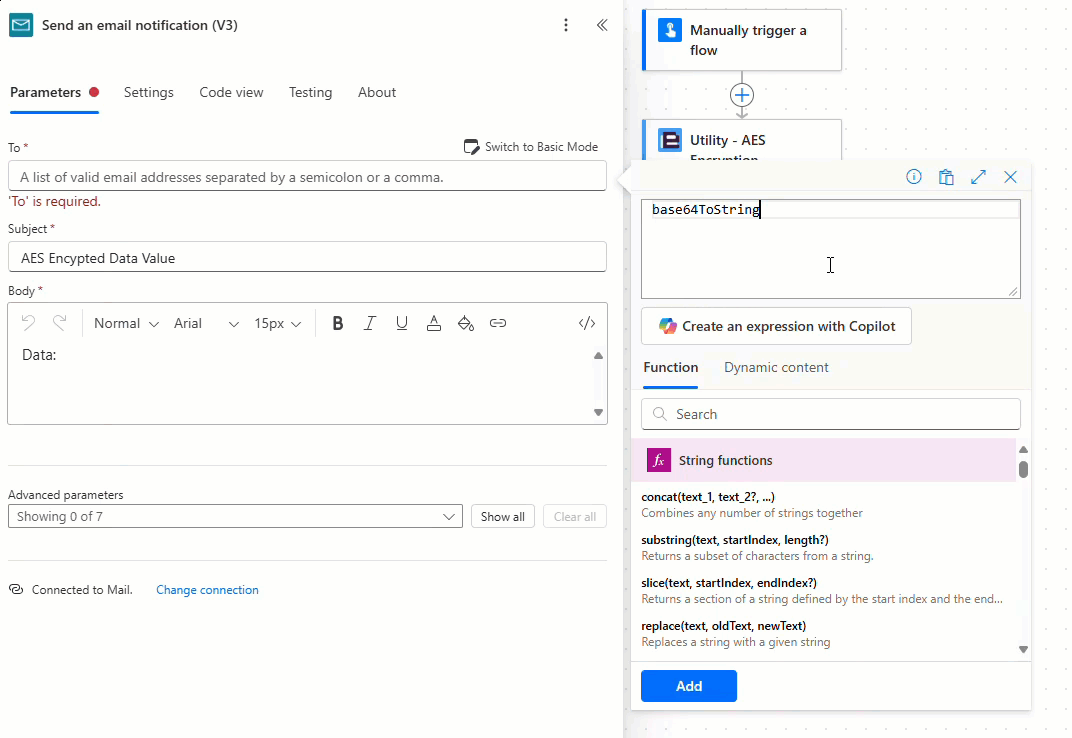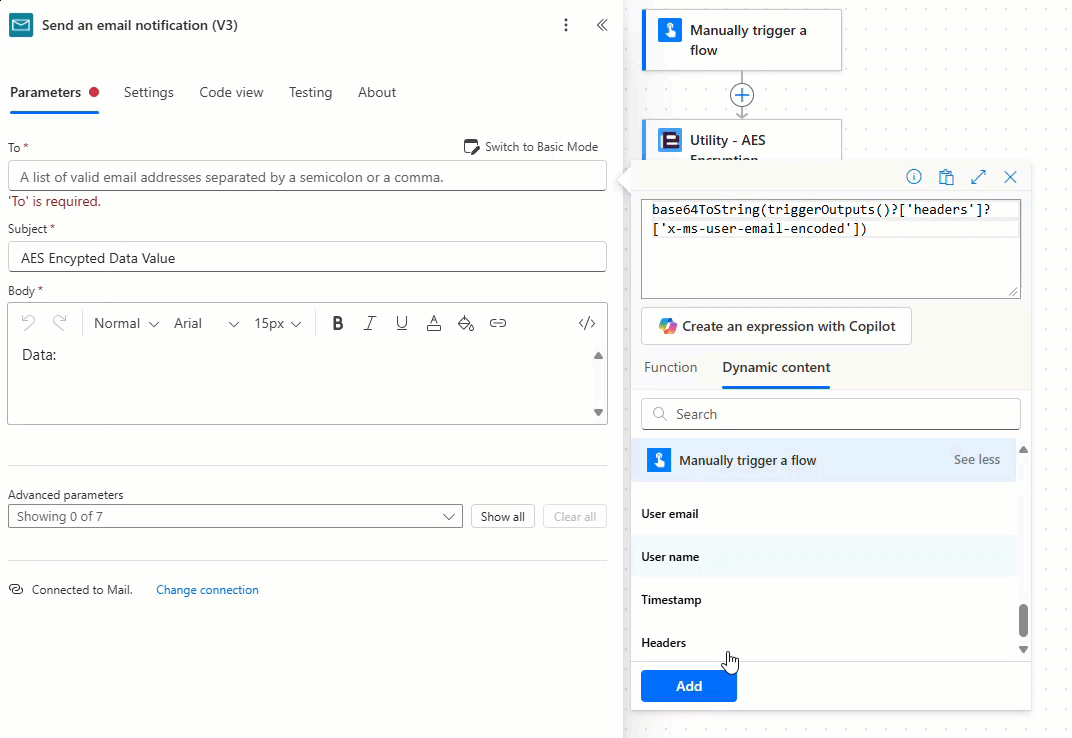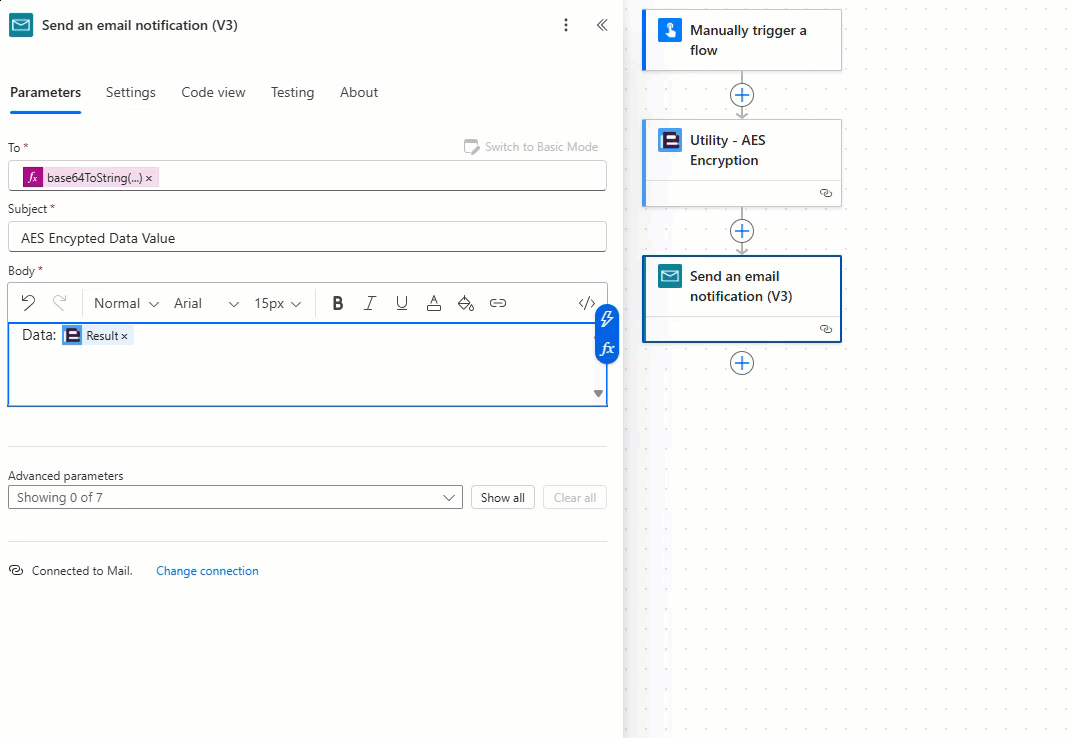
The encryption flow is now complete! Let’s test the flow.
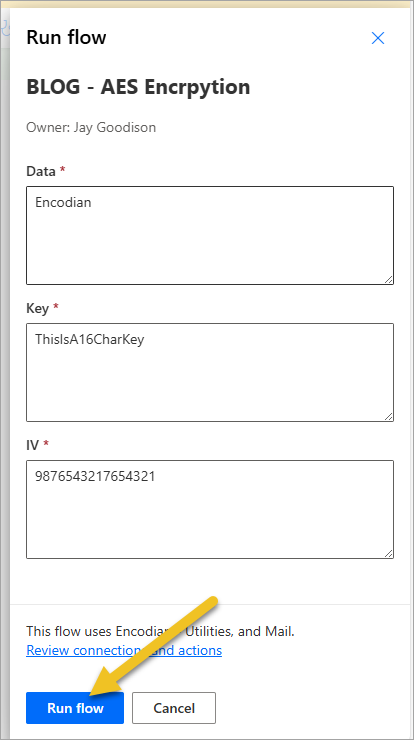
This generated the following email:
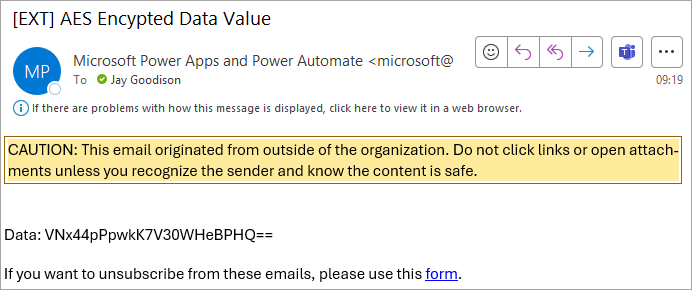
Building on our previous flow, lets now decrypt the data value sent within the email.
Consider the following basic and manually triggered flow:
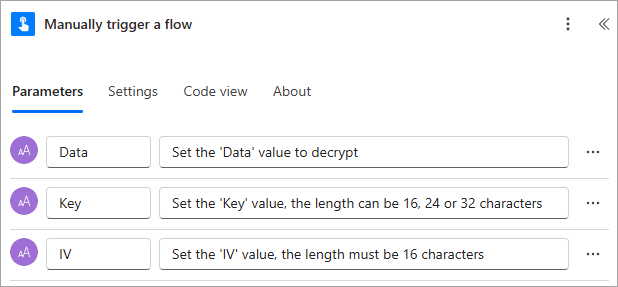
Upon triggering the flow, the user will be prompted for the following values:
1. Add the ‘Utility – AES Decryption‘ utility action
1.a Data: Select the ‘Data’ property provided by the trigger action
1.b. Input Type: Select ‘BASE64’
1.c. Key: Select the ‘Key’ property provided by the trigger action
1.d. Mode: Select ‘CBC’
1.e. Initialization Vector: Select the ‘IV’ property provided by the trigger action
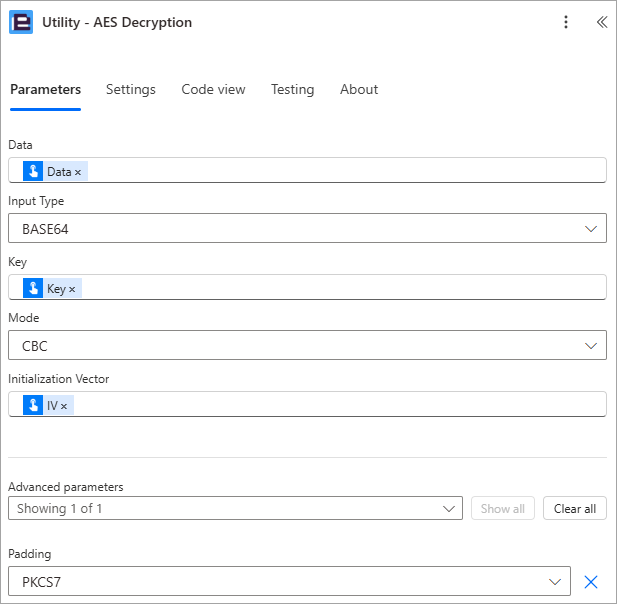
The ‘Utility – AES Decryption‘ utility action will return the decrypted data value contained within the ‘Result’ property. For demonstration purposes I will send the ‘Result’ property in an email to the user who triggered the flow.
Add and configure the ‘Send and email notification (V3)’ action as required, noting that when using the new Power Automate user interface the ‘User email’ property provided by the ‘Manually trigger a flow’ action is encoded as a base64 value which must be converted to a string using the ‘base64ToString’ expression as detailed below:
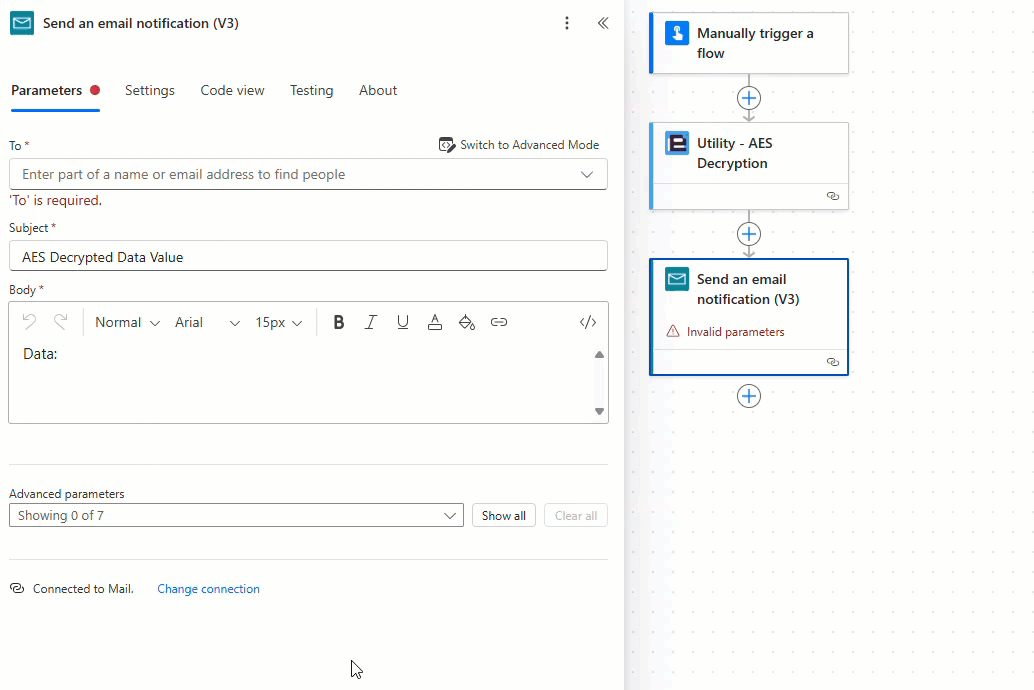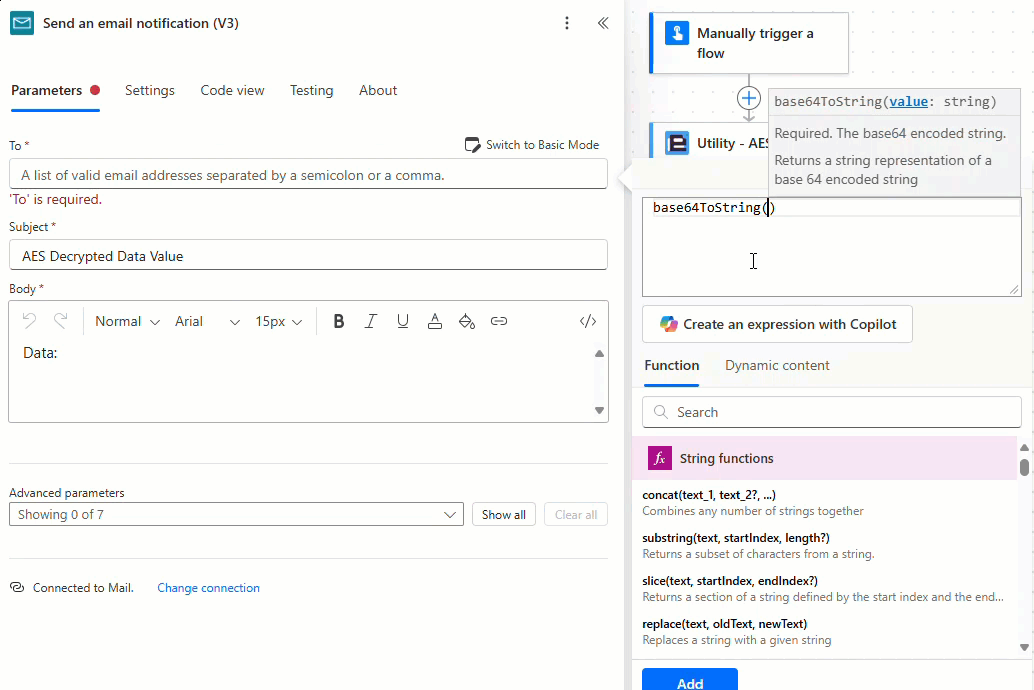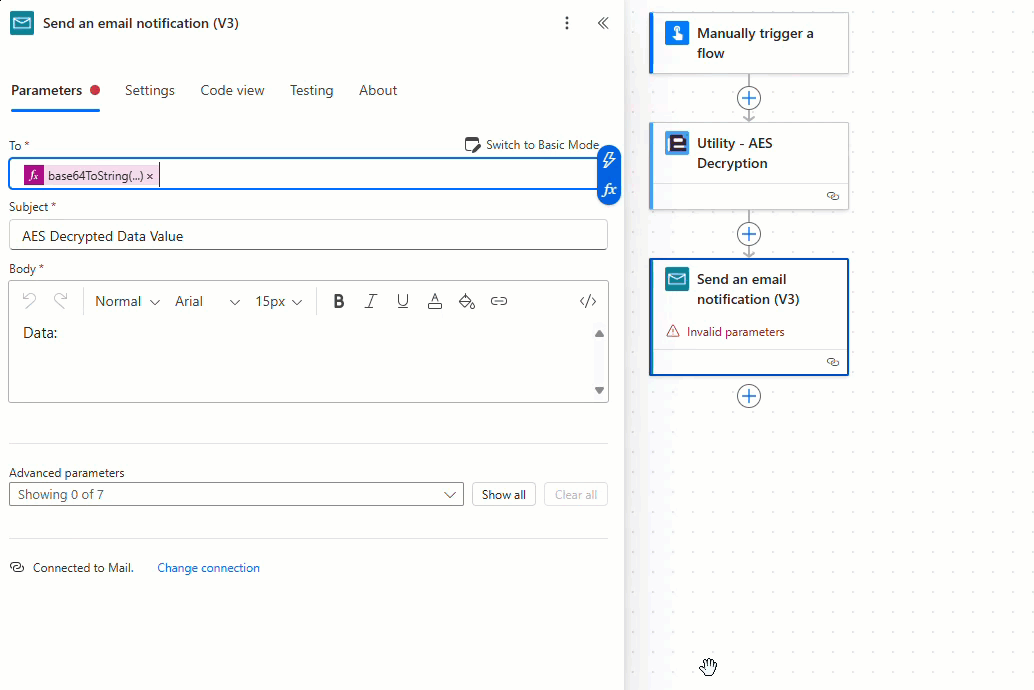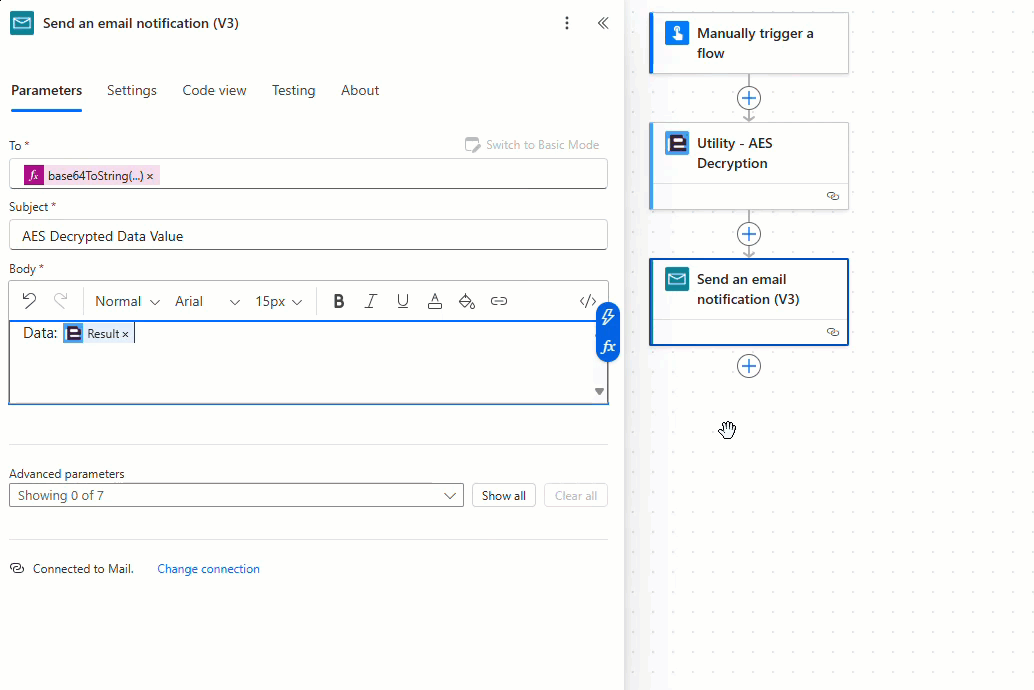
The decryption flow is now complete! Let’s test the flow.
NOTE: The ‘Input Type’ (Data Format), ‘Key’, ‘Mode’ and ‘Initialization Vector’ values must be the same values used to encrypt the ‘Data’ value
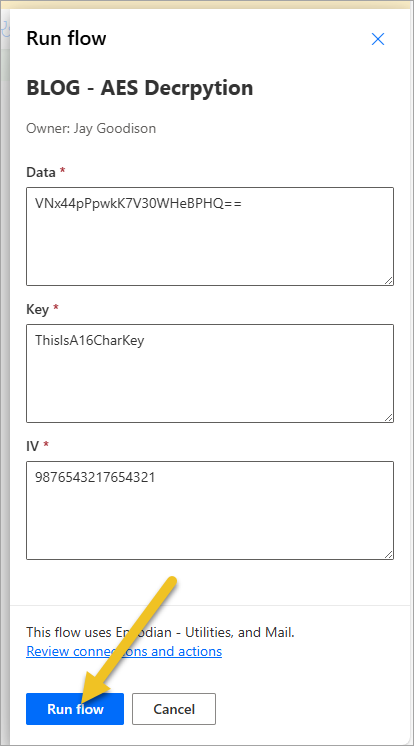
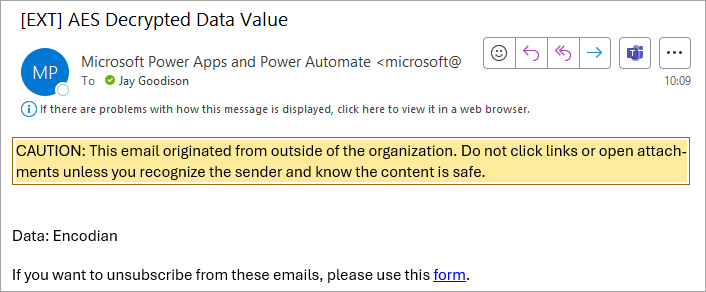
This generated the following email:
Search 150+ Actions to see how Flowr can save you time
Sign up for your free 30-day trial; no cards, catches, or contracts.
CEO